Frequently Asked Questions
How is the PassWindow challenge displayed at different screen resolutions?
The PassWindow challenge pattern presented on the computer screen can easily be resized and moved around on the screen by the user. The size and position is then stored as a cookie in the user's web browser or alternatively on the system server for future reference, so you only ever have to do it once.
Why not try our demo to see the process for yourself?
Do I need to reposition the challenge image each time?
No. The authentication script would simply record your preferred challenge image location and proportion and save this information to a cookie in your browser. If the service detects your cookies are disabled then alternatively the information can be recorded on the server as part of your user profile on their database.
This way, each time you need to authenticate in the future, the pattern is in the correct position for your card.
I am having trouble recognizing some of the numbers in the pattern. Is this normal?
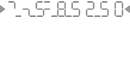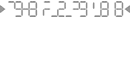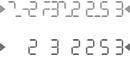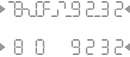 Dont worry – you will quickly learn how to recognize the numbers within the noise. The human brain has a remarkable ability to recognize familiar characters, even when they are surrounded by clutter. The authentication management software at the server end of the transaction will be monitoring your responses and adjust the patterns to make them easier for you every time you authenticate.
Dont worry – you will quickly learn how to recognize the numbers within the noise. The human brain has a remarkable ability to recognize familiar characters, even when they are surrounded by clutter. The authentication management software at the server end of the transaction will be monitoring your responses and adjust the patterns to make them easier for you every time you authenticate.
The animation is too slow or fast, can this be changed?
Yes, the animated challenge speed can be easily modified according to your preference by the server, in fact most implementations will detect the speed of your response and adjust the animation based on your authentication history.
What is the difference between the animated single digit challenges and the static multi digit ones?
Both challenge methods are effective authentication methods however the animated method shown in this video is much more resistant to long term trojan analysis than the static version with the same sized key pattern, requiring over 1000 times more interceptions by an attacker with total control of your computer. This is well beyond any normal usage even with many years of targeted interception and analysis.
The static challenge method works well on non electronic display media such as printed on documents or packaging, the interception value can be easily increased by adding extra columns and rows to both the key and challenge pattern.
A simple guideline is to use larger key patterns for applications which will include static media.
Are transparent cards more expensive than regular white ID cards?
No the costs for transparent cards should be exactly the same as regular white cards.
Most raw plastic from the factory begins in a transparent form to which the specific colour is added during the manufacturing process such as white.
What if somebody looks over my shoulder while I'm using it?
The PassWindow system works by sending a different and unique challenge pattern each time it is used to authenticate a user. This means that even if someone is watching you use the card and sees the digits you are entering on the screen, they can't use those numbers to falsely authenticate as you.
Also, because the PassWindow key pattern is made up of random LCD-display-like segments, even if the shoulder surfer sees your key, the arrangement cannot be easily remembered or communicated, as would be the case with a static CVV number or ordinary password.
What if someone takes my card and photographs or photocopies it?
 A tint printed over the transparent PassWindow card region prevents PassWindow key patterns from being easily photocopied or photographed, and renders the pattern very difficult to see under normal conditions. However, placed against a backlit display, the digits can easily be read.
A tint printed over the transparent PassWindow card region prevents PassWindow key patterns from being easily photocopied or photographed, and renders the pattern very difficult to see under normal conditions. However, placed against a backlit display, the digits can easily be read.
What if someone steals my card?
PassWindow is designed to be used as a second-factor authentication method. This means it should be used in conjunction with a memorized component, such as a username and password. Therefore, to authenticate, the user must provide 'something they know' – their username and password – along with 'something they have' – their PassWindow-embedded identification card.
Using these two factors together, it is possible to prevent people falsely authenticating as the legitimate owner of the card, even if the physical card is lost or stolen.
Why is PassWindow superior to CVV2 and should they be used in conjunction?
The Card Verification Value (CVV) is a number that is typically printed on the back of a credit card, which must be input in conjunction with one's other credit card details when making 'card not present' purchases, such as when one makes an online transaction.
This number is generated cryptographically by the issuing bank using the details of the credit card; however, this number is only printed on the card, it is not stored on the card's magnetic stripe.
Card vendors use this code to ascertain whether the person conducting the transaction either has the card in their possession, or has at least seen the card, or communicated with someone who has seen the card.
While CVV provides some level of protection against online credit card fraud in that merchants are required to regularly delete CVV data, it only really protects against the broad scale theft of card data; for example, from a compromised database.
CVV is also susceptible to phishing scams.
While PassWindow might be considered to be similar to CVV, it is far more secure as a result of the following differences:
- The PassWindow key pattern cannot be easily read, remembered, photographed, or photocopied.
- The PassWindow key pattern cannot be verbally communicated or easily transmitted via computer.
- It is impossible for a phishing scam to generate a valid challenge pattern – alerting the user that the request is being made by a different entity.
- To authenticate with a PassWindow embedded card, the user must have the physical card in their immediate possession.
- The numbers that are revealed when the key and challenge patterns are combined is only used once. So, even if this code is intercepted, it cannot be used for future transactions.
Is the PassWindow key pattern information stored on the magnetic strip?
No part of the PassWindow key pattern is stored on the card apart from the printed pattern in the transparent region of the PassWindow-embedded card. This means that even if you use your card in a compromised ATM fitted with a skimming device, an attacker will not be able to successfully authenticate as you to make online transactions.
How does PassWindow thwart man-in-the-middle-based attacks?
The existence of key-logging and screen-capturing software represents a significant threat to the security of one's electronic data and is commonly used by hackers to obtain usernames, passwords, credit card details, etc. However, attacks of this nature remain fairly uncommon despite media hype.
Regardless, addressing this threat was one of the key design considerations in the development of PassWindow.
Assuming a hacker has infiltrated the target computer such that they are able to run key-logging and/or screen-capturing code, thereby capturing all computer activity, the security of PassWindow follows a predictable trajectory that can be managed so as to completely eliminate the threat of this kind of attack.
For a hacker to calculate enough of the user's PassWindow key pattern to make a reasonable guess about what it is, a minimum of several thousand interceptions must be made for even simple small sized key patterns.
If we generously assume that the target of the attack uses their card to log in or conduct a transaction once per day, it would require the hacker to successfully intercept all login attempts over the course of many years, or decades for the higher-complexity implementations that are commonly used for critical applications. In comparison the same trojan attack can bypass the equivalent time based token authentication in just 1 user interception.
PassWindow's security is also augmented using various proprietary techniques that drastically increase the number of successful interception attempts required to make reasonable guesses at the key pattern.
Much of security strength is increased exponentially by configuring a larger key pattern for the user; our extensive testing and analysis has shown that even with relatively small key patterns of 9 or 12 columns if configured properly are well beyond trojan analysis in any meaningful timeframe.
To complete the picture, with the PassWindow Authentication Manager it is possible to schedule card renewal at particular time intervals or after the user has reached a certain number of authentications, rendering it impossible for a hacker to obtain enough interceptions to have any meaningful chance at guessing the key pattern.
PassWindow's advantage is that in all likely scenarios, even with an extremely dedicated hacker, it would take in the order of years of hacker surveillance, and even this possibility can be negated through the correct use of the PassWindow Authentication Manager software.
How is PassWindow superior to existing authentication systems like RSA's SecurID or VASCO's Digipass?
Existing authentication systems use a hardware token that contains sophisticated electronics that generate new authentication codes at given time intervals – usually around 30 seconds or a minute. The clocks on the server and the hardware token are synchronized, allowing the server to be reasonably sure that the person entering the code is in possession of the hardware token.
The PassWindow authentication method is superior to hardware token based methods for the following reasons:
- PassWindow is significantly less expensive to implement and manage.
- PassWindow contains no electronics, so it never runs out of batteries or experiences clock synchronization problems.
- Unlike the codes generated by SecurID, the PassWindow key pattern cannot be easily communicated, which means it's more secure against social-engineering-based attacks.
- PassWindow is more secure against Man-In-The-Middle (MITM) attacks.
- You can easily distribute PassWindow-embedded cards through your existing card distribution infrastructure.
- Unlike hardware tokens, PassWindow-embedded cards introduce no additional support costs.
How does PassWindow protect against brute-force cracking techniques?
A brute-force attack generally involves continually probing an encrypted piece of data with many password keys to see if any succeed in producing a rational output, thereby hinting that the key is likely correct.
Because each PassWindow challenge/solution pair can suggest a number of possible keys, the only way it is possible to crack the PassWindow system is through statistical analysis of many known challenges/solutions intercepted over a compromised Internet connection.
So, while a brute-force attack is theoretically possible in this sense, it is prevented by the fact that it would take an attacker a very long time, in the order of months or years with normal use, to intercept sufficient challenge/solution pairs to compromise the user's PassWindow key pattern.
Therefore, unlike conventionally encrypted data, PassWindow is not susceptible to brute-force attacks.
Could an attacking trojan try to match keystrokes against challenge frames?
By monitoring a user's keystrokes a trojan could theoretically try to match the timing of these against the challenge frame shown and thereby speed up the necessary number of interceptions to try to deduce the users key. In reality this is a very unlikely attack as users are seldom as precise in their keystroke timing as they would need to be and a variety of unknown factors could warp the results such as challenge network loading times.
Part of the added security strength of the animated challenge method is to obfuscate the exact digits a user enters against which frame the user has read them from; there are two simple methods to prevent this type of potential Trojan analysis being done against a user.
- A basic defence is to make the password field hidden which requires the user to memorize the digits and only when they are ready and click a submit button does the password field become visible.
- The second method is to analyse this behaviour in the same way as the Trojan might. This would involve actively monitoring in the background the user’s password keystrokes and their associated timing with simple and then on the server side deduce upon submission if the user really is pressing the password digits at the same time as the frames themselves are being shown. The authentication manager can then decide to actively increase the frame rate of the user’s future authentication challenges or even provide a simple warning message to the user explaining their login behaviour is making their key less secure.
In practise this possibility can be easily prevented without any active interference to the user.
Couldn't a hacker just analyze a set of challenge keys to determine which segments never get used?
The PassWindow challenge pattern generator produces line segments that randomly superimpose segments on the key, so this technique cannot be used to gain information about the PassWindow key pattern on your card.
Is PassWindow superior to biometric authentication techniques?
Biometric techniques, such as fingerprint or retinal scanning seek to authenticate the user based on properties unique to their bodies. While countless Hollywood movies might leave us with the impression that biometric identification systems are the gold standard of personal authentication, they are problematic for a number of reasons, a few of which are often borne out in the plots of said movies.
For example:
- It is impossible to reissue a user's compromised biological key pattern – imagine never being able to change the locks on your house, despite knowing that unwanted people have the key. Reissuing a new PassWindow card is simple.
- In the case of fingerprint biometrics, the user leaves a copy of their key on everything they touch. PassWindow cards are usually kept tucked away in one's wallet.
- Biometrics requires expensive hardware. PassWindow requires no additional hardware.
- Deploying and maintaining remote biometric hardware is logistically challenging. Deploying PassWindow follows the same deployment logistics as normal cards.
- A user cannot delegate their rights. A PassWindow card can be given to another user to use.
- It is easy to spoof most biometric authentication systems. PassWindow is very difficult to spoof.
What key size configuration values are secure?
From our extensive analysis deduced by many independent international cryptographers and specialist mathematical pattern analysts there are a few simple rules for exponential key strength when choosing a PassWindow configuration.
- Key column width - Simply adding extra matrix column's to a key pattern exponentially increases the strength of the overall method. The increase in statistical difficulty from 15 to 18 columns is exponentially greater than the increase from 12 to 15.Of course there is nothing to stop you using a 50 column key pattern.
- Authentication digit to animation frame ratio - For a particular animated configuration there might be for example 10 overall single digit frames with a 6 digit authentication code request, counter intuitively a smaller 4 digit code is actually more difficult to analyze as the ratio between digits to frames will have increased. This effect is exponential as the increase from 6 to 4 digits in 10 frames is far greater than the difficulty increase from 8 to 6 digits in 10 frames. There is no cost to user convenience by simply adding more frames to the challenge patterns.
- Other simple configuration settings which can drastically increase the overall PassWindow security include, extra pattern rows, increasing obfuscation segment frequency, larger character set possibilities and modifications to the animated frames and general user method however these all come at a convenience cost for the end user.
A general suggestion from our own analysis for the smallest secure patterns would be 9 column key pattern for normal user authentication and 12 column key patterns for financial systems requiring individual transaction authentication.




