PassWindow has signifigant security advantages over all existing software, electronic and mobile-phone based authentication methods. PassWindow's segment matrix pattern provides an ideal mix of security, usability, and flexibility.
The universally-recognizable characters are dispersed randomly throughout the segment matrix pattern. The obfuscational noise provides added security without reducing readability. This is because the human brain can easily distinguish common characters despite slight obfuscation – similar to how CAPTCHA systems work, but far more readable.
Even if an attacker intercepts, compromises or controls the user's entire computer or device with a key logger, screen capture trojan or malware program, the attacker will need to wait well beyond the life of that user's card to gather enough data to successfully derive the user's key pattern.
PassWindow cards require no electronics. By relieving the client of almost all technology requirements, PassWindow centralizes the high-tech aspects at the secure, server-side of the transaction, inaccessible to hackers.
PassWindow key patterns are pre-analysed under the most intensive security conditions; i.e., complete terminal compromise and control by an attacker. Any potential information loss is very predictable and easily prevented by the inherent flexible nature of the method, thereby ensuring complete protection against even the worst possible online attack scenarios.
PassWindow is the only non-electronic device that can unequivocally verify transactions before they are made. The PassWindow Authentication server encodes your destination account details or some other transaction information into the challenge image, making it impossible for funds to be covertly diverted by third parties. This feature can potentially eliminate all online banking fraud and is unique to PassWindow. See the flash animation at the top of this page for a clear explanation.
No. Many people are suprised to discover the random card key pattern is simple a printed matrix of segments the same as any barcode. All the character visualization calculations are done by the server which creates the animated challenge picture the card sits in front of.
Its PassWindow's extremely low-tech approach which gives it such a low attack surface, leaving attackers with no hi-tech approaches they would normally employ against electronics.
No. The animated screen challenges are simply gif images, a universal web image format. This means that any ordinary browser on any device will display the challenges with no effort required by the user.
Interestingly the challenges can also be printed on paper such as documents so users can authenticate using a pencil and paper.
The PassWindow challenge pattern presented on the computer screen can easily be resized and moved around on the screen by the user. The size and position is then stored as a cookie in the user's web browser or alternatively on the system server for future reference, so you only ever have to do it once.
Why not try our demo to see the process for yourself?
No. The authentication script would simply record your preferred challenge image location and proportion and save this information to a cookie in your browser. If the service detects your cookies are disabled then alternatively the information can be recorded on the server as part of your user profile on their database.
This way, each time you need to authenticate in the future, the pattern is in the correct position for your card.
Yes, the animated challenge speed can be easily modified according to your preference by the server, in fact most implementations will detect the speed of your response and adjust the animation based on your authentication history.
No the costs for transparent cards should be exactly the same as regular white cards.
Most raw plastic from the factory begins in a transparent form to which the specific colour is added during the manufacturing process such as white.
 A tint printed over the transparent PassWindow card region prevents PassWindow key patterns from being easily photocopied or photographed, and renders the pattern very difficult to see under normal conditions. Your physical proximity security should always be considered seriously no matter what security action you are performing and PassWindow is just as susceptible to physical attack as other methods in this regard.
A tint printed over the transparent PassWindow card region prevents PassWindow key patterns from being easily photocopied or photographed, and renders the pattern very difficult to see under normal conditions. Your physical proximity security should always be considered seriously no matter what security action you are performing and PassWindow is just as susceptible to physical attack as other methods in this regard.
PassWindow is designed to be used as an online second-factor authentication method. This means it should be used in conjunction with a memorized component, such as a username and password. Therefore, to authenticate, the user must provide 'something they know' – their username and password – along with 'something they have' – their PassWindow-embedded identification card. A random thief or lost card would not be recognizably associated with a victims username or password.
In fact this physical proximity security issue applies to all physical authentication devices and PassWindow is no different. Hardware tokens can be quickly replaced with replica dummies designed to capture a local pin number. Mobile phones have a large attack surface and are suceptible to both online, remote and physical proximity attacks. Biometric authentication can be spoofed.
The Card Verification Value (CVV) is a number that is typically printed on the back of a credit card, which must be input in conjunction with one's other credit card details when making 'card not present' purchases, such as when one makes an online transaction.
This number is generated cryptographically by the issuing bank using the details of the credit card; however, this number is only printed on the card, it is not stored on the card's magnetic stripe.
Card vendors use this code to ascertain whether the person conducting the transaction either has the card in their possession, or has at least seen the card, or communicated with someone who has seen the card.
While CVV provides some level of protection against online credit card fraud in that merchants are required to regularly delete CVV data, it only really protects against the broad scale theft of card data; for example, from a compromised database.
CVV is also susceptible to phishing scams.
While PassWindow might be considered to be similar to CVV, it is far more secure:
The existence of malware with man-in-the-middle capabilities represents a significant threat to the security of the online community and is commonly used by hackers to obtain usernames, passwords, credit card details and enable fraudulent transaction authentication etc.
Mobile SMS and OTP hardware token authentication provides little protection against this threat.
PassWindow has the unique ability to encode specific transaction information directly into the visual challenge thereby preventing a man-in-the-middle attack, whats more this mutual authentication is done passively by the user who simply visually checks the information rather than long complicated manual processes employed by high end transaction signing tokens.
Existing authentication systems use a hardware token that contains sophisticated electronics that generate new authentication codes at given time intervals – usually around 30 seconds or a minute. The clocks on the server and the hardware token are synchronized, allowing the server to be reasonably sure that the person entering the code is in possession of the hardware token.
The PassWindow authentication method is superior to hardware token based methods for the following reasons:
No, from the very beginning we have analyzed this threat ourselves and found the results are very predicatable and not practical for an attack even under the ideal circumstance for an attacker.
Primarily our server analyzes the key and challenge interactions ourselves and introduces enough entropy to ensure an attacker will never gain enough information to determine the key pattern over the life of the card.
We assume this analysis is being done right from the beginning and by simple pattern manipulation and authentication behaviour monitoring ensure the required interceptions are well beyond an attackers reach.
PassWindow's security is also augmented using various proprietary techniques that drastically increase the number of successful interception attempts required to make reasonable probabalistic statistical deductions at the key pattern.
Much of security strength is increased exponentially by configuring a larger key pattern for the user; our extensive testing and analysis has shown that even with relatively small key patterns of 9 or 12 columns if configured properly are well beyond trojan analysis in any meaningful timeframe.
To complete the picture, with the PassWindow Authentication Manager it is possible to schedule card renewal at particular time intervals or after the user has reached a certain number of authentications, rendering it impossible for a hacker to obtain enough interceptions to have any meaningful chance at guessing the key pattern.
PassWindow's advantage is that unlike electronics where security strength is hardcoded into the chips PassWindow challenges being a simple browser image are able to manipulate the overall security and usability even after the card has been deployed.
By monitoring a user's keystrokes malware could theoretically try to match the timing of these against the challenge frame shown and thereby speed up the necessary number of interceptions to try to deduce the users key. In reality this is a very unlikely attack as users are seldom as precise in their keystroke timing as they would need to be and a variety of unknown factors could warp the results such as challenge network loading times.
Part of the added security strength of the animated challenge method is to obfuscate the exact digits a user enters against which frame the user has read them from; there are two simple methods to prevent this type of potential malware analysis being done against a user.
In practice this possibility can be easily prevented without any active interference to the user.
From our extensive analysis deduced by many independent international cryptographers and specialist mathematical pattern analysts there are a few simple rules for exponential key strength when choosing a PassWindow configuration.
A general suggestion from our own analysis for the smallest secure patterns would be 9 column key pattern for normal user authentication and 12 column key patterns for financial systems requiring individual transaction authentication.
At first glance the visual keys may appear simplistic which could lead you to question how many potiential unique keys there are available.
In simple language let's take the 12 column keys used in our demo, there are 62 available segments with 4,611,686,018,427,387,904 possible combinations. Approximately 30% of those are too light, dark or contain unwanted characters. This leaves us with such a huge number of potiential keys that we never need repeat the same key twice, ever.
SMS-based authentication/verification: ![]()
Smart Card / RFID Card / Magnetic Strip: ![]()
LiveCD security: ![]()
Text Passwords: ![]()
User perception of security is a very important component of any security chain; often, users are forced to accept the purported security of a mysterious electronic device, which often breeds scepticism in their mind, particularly if it is viewed as an inconvenience.
A great security system is no different to having none at all if your user base is unable or unwilling to use it. The average online user today has little to no trust in software and hardware authentication systems that they cannot understand.
PassWindow's simplicity provides a system that even children can see and understand its inherent security.
A man-in-the-middle attack is where the attacker makes independent connections between the service and user and relays messages between them, making them believe that they are talking directly to each other over a private connection when in fact the entire conversation is controlled by the attacker. This type of attack commonly circumvents many types of online authentication systems.
The latest trojans, including the Man In The Browser (MITB) attacks, which are defeating the common OTP-style hardware tokens are defended by PassWindow's ability to embed the actual transaction value or type directly into the encoded pattern, thereby alerting the average user to the exact nature or value of the transaction they are authenticating.
This prevents the attacker from switching account details and relaying the generic authentication codes usually given by electronic token devices.
Advanced bulky electronic tokens with attached keypads and inbuilt transaction signing can provide a complex type of user-actioned transaction authentication with a heavy usability cost where the user must enter all the challenge and transaction information into the devices; however, it has been revealed that the complex nature of the method has allowed criminals to bypass even this high level of electronic security by simply programming the user actions under the guise of device resynchronization.
The passive transaction authentication method provided by the PassWindow method protects against user programming, and in doing so allows protection against even the most pernicious malware or social engineering methods.
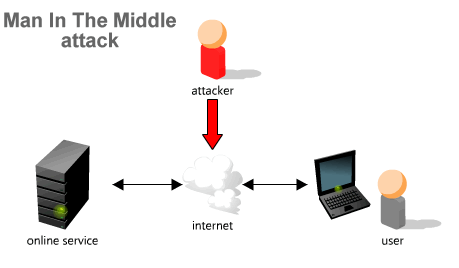
Attacker hijacks entire online connection or tricks the user into visiting the attacker's fake website.
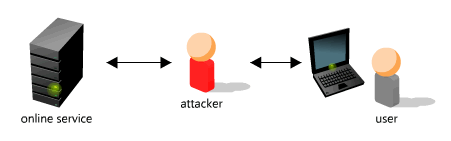
He then inserts himself between the user and the user's real online financial service, controlling all communications.
While the attacker can transfer the authentication challenge images into their fake website the user is viewing, they cannot modify the animated challenge pattern which contains specific transaction information for the user.
In this challenge the random password digits follow the letter P and last 3 digits of the account destination follow the letter A
Superimposed key and challenge patterns
![]() = P34896 A255
= P34896 A255
The extra encoded information could be almost any unique transaction specific information including name, date, value, IP address or a specific message to the user.
The rotating challenge digits force a user to visually observe the transaction information

With most electronic tokens, the authentication is time or event based and lacks any information about the type or amount of the transaction being verified. The attacker simply requests that the user either enter in their valid authentication code or validate a numeric challenge.

Once the token user believes he is interacting with his genuine financial service, the attacker requests multiple authentications under various innocuous pretences. The user's account is then emptied in the background.
PassWindow is unique in being able to increase the relative security of its challenges without needing to reissue the user's authentication token.
The size of the key can be varied to suit your security needs:
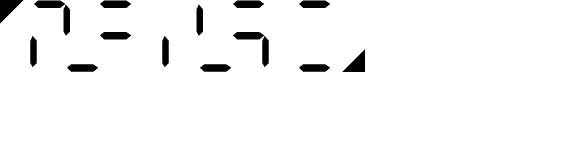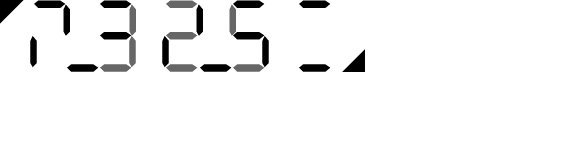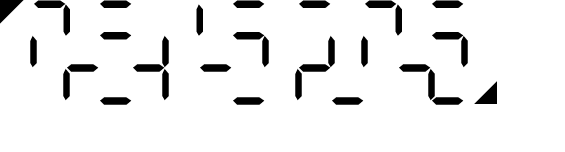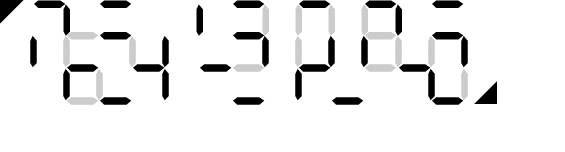
|
Challenge: | |
| User key: | ||
| Composite of key and challenge: |
Unlike many other authentication methods, the visual aspect to the key pattern is extremely resistant to common social engineering tricks, such as convincing the user into giving out a valid key code either online or over the telephone.
However, a user is always vulnerable to physical attack or surreptitious video surveillance. Because PassWindow resides on the card itself and is not an electronic device, the key is kept securely in the user's wallet or purse as opposed to dangling freely on a keychain or loose on their office desk – an immediate advantage over SMS and hardware tokens. Video surveillance can also be mitigated through a variety of means, ranging from simply applying a darkened tint around the pattern when it is printed to applying specialized transflective laminate overlays.
Key patterns can be obscured from discrete video surveillance according to your security requirements or can be customized according to a particular user's authentication history and circumstances.
Visualization of the pattern only occurs when it is superimposed upon the backlit electronic display
The user or authentication management is able to fully customize this level of personal protection on a per user basis if necessary.

Please note: There is nothing special about the tinting shown above, laminates are not necessary, it is printed with the regular printer with merely a grey shade on the key pattern image.
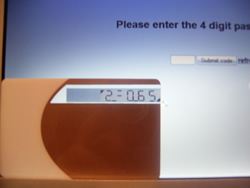
The backlit screen of normal computer displays allow the user to clearly see the authentication numbers through the tinting.